Convergence & Acquisition: Why Is the Cyber and IAM Technology Market Currently So Dynamic?
It’s not only in the kingdom of AI that checkbooks have been wide open in recent years. In cybersecurity as well, acquisitions are happening at a sustained pace. The amounts are sometimes less staggering, but the Monopoly game is no less intense, especially on the IAM, PAM, and CIAM technology side.
The latest move: Delinea, a well-known player in Privileged Access Management (PAM), has just announced the acquisition of StrongDM. A strategic transaction aimed at strengthening its capabilities around non-human identities, following the acquisition of Authomize less than two years ago, which had already reinforced its cloud access management posture.
A Quick Overview of the IAM and Cyber Technology Transfer Market
Last year, the heavyweight Palo Alto made a major move by acquiring CyberArk for nearly $25 billion, a giant that had itself acquired Venafi the previous year to strengthen machine identity management. In the CIAM (Customer Identity and Access Management) space, Okta is not to be outdone with the recent acquisition of Axiom Security, aimed at consolidating its Just-In-Time access capabilities, in a more targeted approach than the acquisition of Auth0 in 2021.
It would also be difficult to overlook the acquisition of Wiz by Alphabet (Google) for $32 billion last year, or that of Hashicorp by IBM for “only” $6.4 billion. And other areas of cybersecurity are not being left behind either, rest assured, with ServiceNow’s acquisition of Armis and Veza, or Cisco’s acquisition of SnapAttack, not to mention the almost constant activity of the Thoma Bravo fund, known for its serial buy-and-sell strategy, particularly around Sailpoint, which had in turn acquired Osirium and SecZetta in 2023, and which is in the process of finalizing the acquisition of DarkTrace.
So what explains all this enthusiasm surrounding IAM, PAM, and machine identity management technologies? What is happening in the world of cybersecurity? Have the cybersecurity giants lost their minds, or is this the foundation of a long-term strategy?
Taking Into Account a Rapidly Evolving Perimeter
Identity at the Heart of the Zero Trust Approach
We have known for several years that identity is the cornerstone of any cybersecurity strategy and is becoming the foundation of the perimeter to be secured, as well as of so-called Zero Trust approaches. Sound IAM management makes it possible to mitigate many modern threats and tactics outlined in the MITRE ATT&CK framework, such as privilege escalation, lateral movement, credential access, and more, by not focusing solely on access and authentication as such, but by taking a broader identity-centered approach.
This is why many of the acquisitions mentioned earlier aim to place identity at the core of existing cybersecurity technologies, thereby offering a broader view and filling certain gaps.
For example, by bringing CyberArk’s PAM capabilities closer to its current activities, Palo Alto Networks aims to deliver end-to-end protection, ranging from network and endpoint security to the management of privileged access to those components.
TIP 01
Put identity at the top of your priorities: do not assume that managing access is enough, identity is the true starting point.
The Impact of AI on Technologies
It would be an understatement to say that “AI” is the buzzword of the moment, and it has been for some time now. It is bringing a number of new paradigms to cybersecurity and to the tools that support it.
All cybersecurity tools want to highlight their AI capabilities, not always as strong as the marketing brochures suggest, and some of these acquisitions help accelerate the journey and avoid missing the moving AI hype train.
But beyond the marketing effect, AI introduces new considerations. For example, one of the topics currently being debated in the IAM sphere is the management of AI Agent-type identities, not quite human, fortunately, but not entirely non-human either, a small thought for Skynet. How should these identities and the access they hold be managed? Who is responsible for what? And how can control mechanisms be implemented when these agents are already deployed in production in many organizations?
Many unanswered questions, but one certainty: to manage agentic identities, you must be solid both on human identities and on non-human identities. It is therefore logical to see many acquisitions enabling vendors to strengthen themselves in one or the other of these identity types in preparation for managing “agents.”
Rationalizing the Number of Cybersecurity Tools
Rationalization through acquisition
Over the past two decades, the cybersecurity tool landscape has “slightly” exploded. It is very likely that you have already seen “summary” placemats like this one:
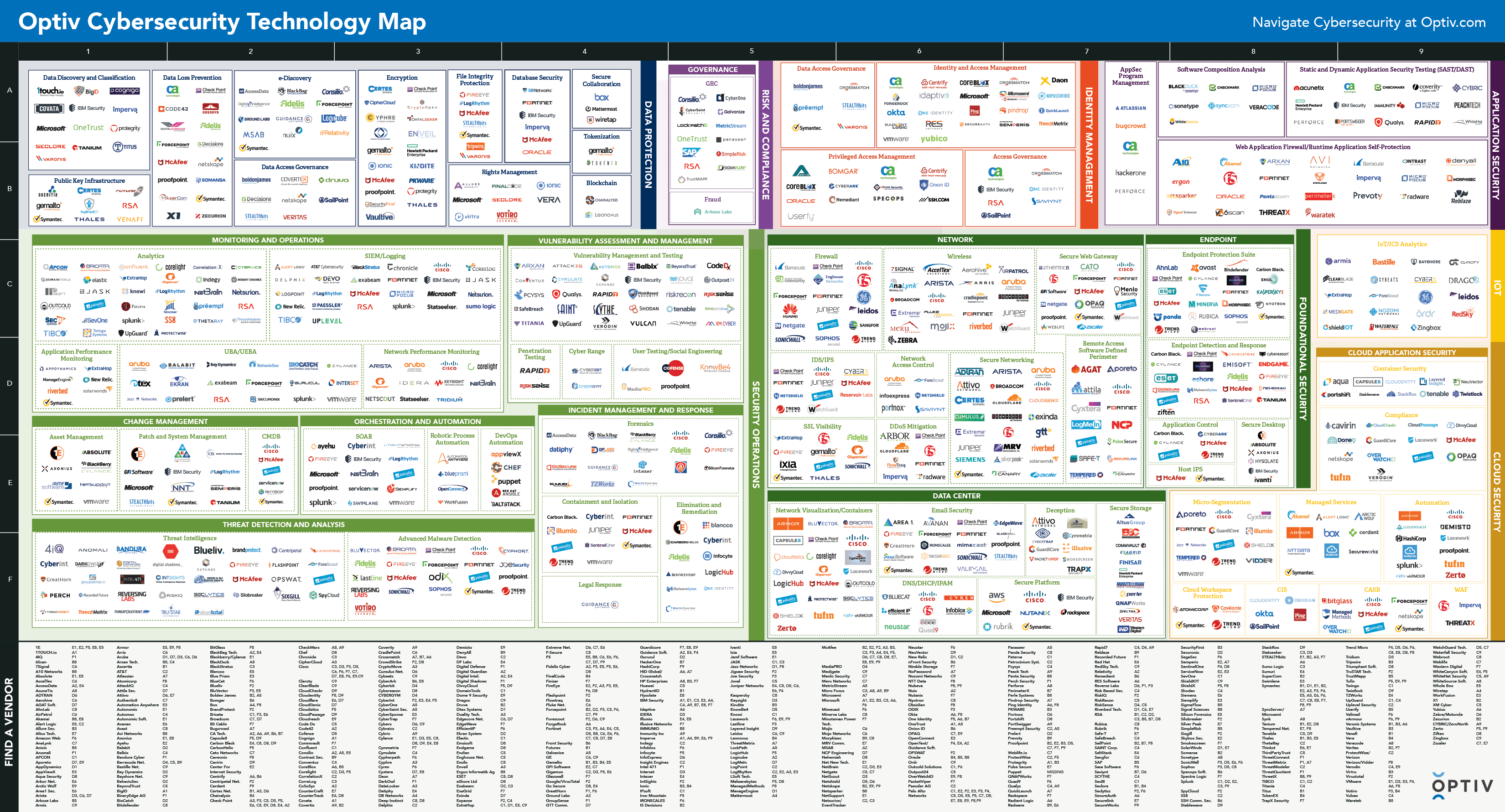
Source : https://www.stationx.net/wp-content/uploads/2024/05/Cybersecurity-Technology-Map-Web-min-1.png
Note that to find your way around, as in large city maps, there are even letters and numbers on the x and y axes in this example. Practical, but concerning and revealing: it shows just how abundant the technologies are and how saturated the landscape has become.
But as we have all learned, technology is only one point of the sacred IT triangle, and we must not forget that technology is nothing without PEOPLE and PROCESS. And this is where this saturation is now hindering organizations.
TIP 02
Avoid blind spots: the triangle also includes PEOPLE and PROCESS. Investing in a tool without considering the other dimensions will bring you more headaches than anything else.
After investing for nearly 15 years in acquiring and deploying numerous tools to support each cybersecurity domain, organizations now find themselves having to maintain very large cyber teams to support dozens of heterogeneous tools, at a time when expertise in the market is scarce.
TIP 03
Rationalize your tool investments: capitalize on the tools already in place to use them fully and follow market trends to avoid unnecessary purchases.
The acquisition, merger, and consolidation trends discussed at the beginning of this article also help address one of users’ needs: fewer tools with more features, so they can be operationalized with fewer people.
Rationalization by Design
This need for functional convergence is not entirely new, and some vendors have, from the outset, chosen a convergent approach, designing their platforms as evolving solutions, not limited to covering a single cyber function. This allows them to control their technology end-to-end by choosing internal development over acquiring other companies, while offering a smooth and unified experience for cybersecurity teams.
We can think, for example, of tools such as Cynet or Saviynt. This approach does not come without challenges and raises questions such as the ability to keep up with market trends and attackers when the vendor must maintain the entire functional stack of the tool. But the effort deserves to be highlighted and encouraged, as this approach places user concerns at the heart of the tools.
TIP 04
Get support from experts: there are professionals whose role is both to advise you on market trends and your cybersecurity investments, and to implement these technologies while taking into account the human transformation they must bring. So call on them, call on us.
